Any organization with an API can be targeted even when they implement APIs or API security.
APIs that provide access to payment information demands more safeguards than, a service that shares images. API security best practices protects APIs from attacks as APIs enable access to sensitive software functions and data therefore are targeted by attackers.
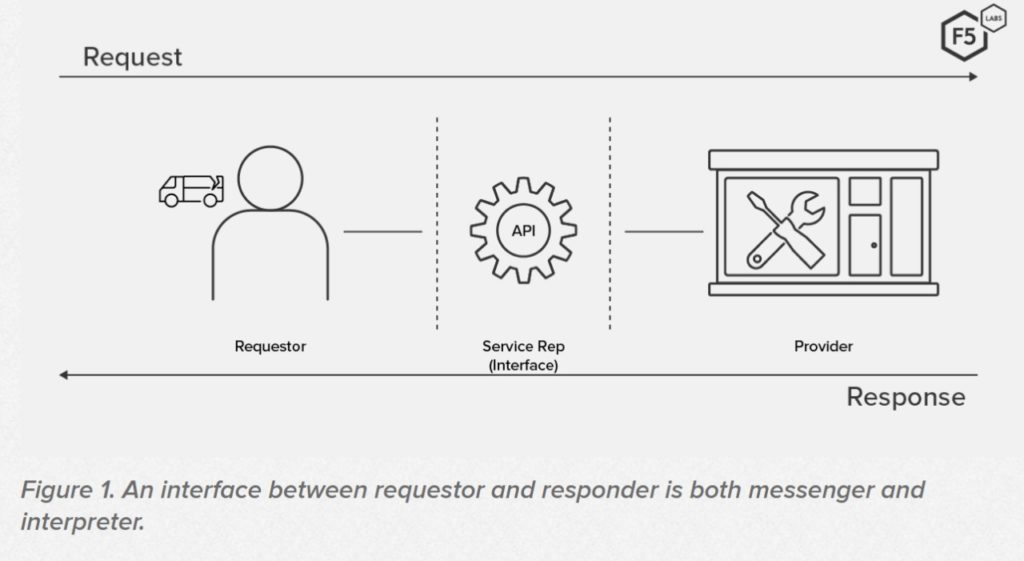
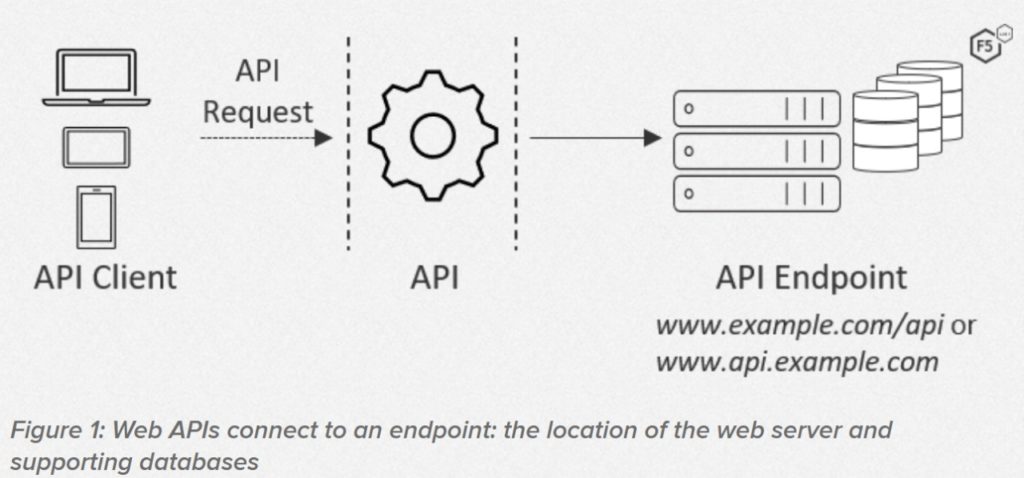
APIs provide a standardized path by which two applications can send data back and forth. An ecommerce site interacts with payment software, shipping software, and other integrations through their respective APIs.
APIs can be built is several ways, but for software integrations with a product you would have to use Rest APIs.
REST APIs transfer data via HTTP. This is similar to sending HTML documents to browsers. This architecture is used by many public APIs and internal APIs (as in microservices). REST APIs are used by Netflix, Uber, and Trello.
You can greatly reduce risks associated with maintaining an API, by following the below points.
API Security Best Practices
- Implement authentication.
- Implement authorization.
- Validate all requests.
- Encrypt all requests and responses.
- Only include necessary information in responses.
- Throttle API requests and establish quotas.
- Log API activity.
- Conduct security tests.
1. Implement Authentication
An API performs authentication before processing a request to verify the identity of the user or program from where the request originated.
APIs generally authenticate using a password or via multi-factor authentication, and/or with an authentication token. This could be a string of characters which could be the unique identifier for a user. To authenticate a request using a token, an API matches the token in the request with one in its database.
Tokens help organizations to keep track those trusted with its resources. OAuth protocol is a widely accepted standard for API user authentication.
This was designed for social login, where users log into third-party applications with passwords without revealing them. As in, me using my Google password to sign into LinkedIn, without LinkedIn storing my password. OAuth is a perfect example for REST API.
2. Implement Authorization
After verifying the identity of a user who sends the request, an API needs a way to grant access to only the authorized resources and methods. For example, a user might be approved to access the API, but is not allowed to add information to the application’s database via the POST method.
Therefore such a request to do so should be rejected. Within a request authorization information can be contained as a token.
Unlike several API types, REST APIs must authenticate and authorize each request made to the server. This is even if multiple requests originate from the same user. REST communications are stateless. That is, each request can be comprehended by the API separately, without mining information from previous requests.
We know that various roles have different permissions, hence authorization too can be governed by user roles. API developers generally adhere to the principle of least privilege. Which states that users should have access to resources and methods demanded for that role alone, and not more.
Predefined roles make it easier to supervise and change user permissions. This inhibits the chances of providing access to sensitive data to the wrong personnel.
3. Validate All Requests
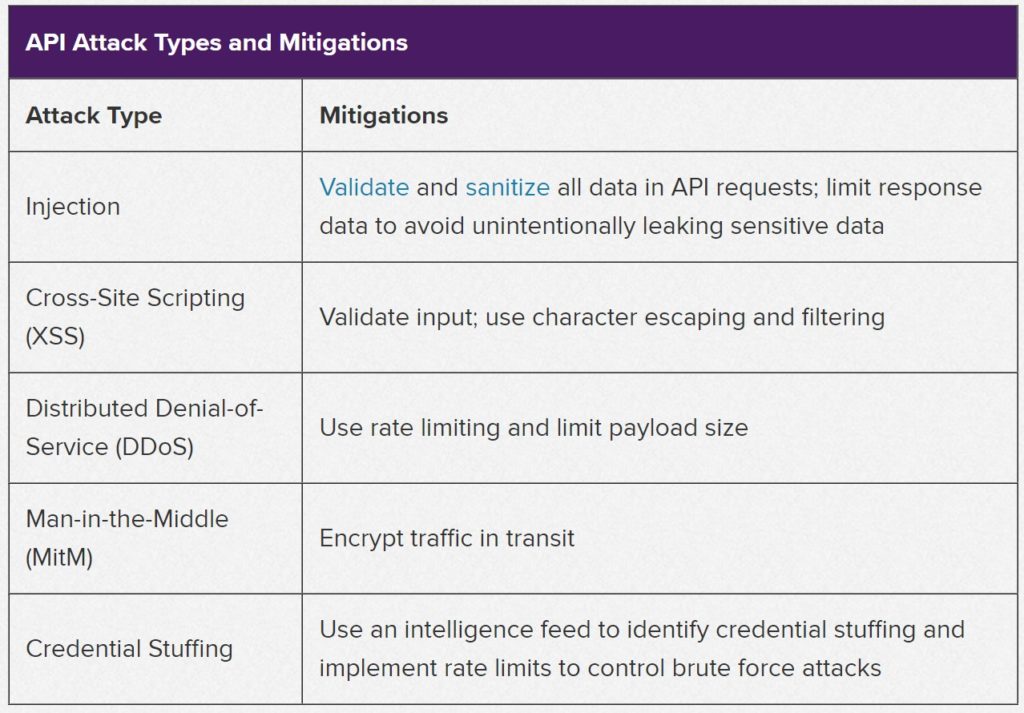
There are chances that sometimes requests from impeccably valid sources could be hacking attempts. Therefore this necessitates that APIs need rules to decide whether a request is friendly, friendly but invalid, or harmful. Harmful as in an attempt to insert harmful code.
An API request is processed only after its contents go through a validation check. This ensures that the request should otherwise never reach the application data layer.
4. Encrypt All Requests & Responses
To prevent MITM (Man In-The Middle) attacks, all data transfers to and from the user to the API server must be appropriately encrypted. In this manner, any responses or requests that are intercepted will not be of use to the trespasser as they will not possess the right decryption method.
As REST APIs use HTTP, encryption can be done via (TLS) Transport Layer Security protocol or a previous iteration, the Secure Sockets Layer (SSL) protocol.
Have you noticed some URLs start with http, while some others with https?
When you browse websites providing sensitive information, like paying bills online – you notice those URLs with the extra “s”. What does that extra “s” mean?
The “s” in ‘https’ means your connection to that website is secure and encrypted. Any data you enter is safely shared with that website. The technology that powers it is called SSL or “Secure Sockets Layer.”
These protocols are standard for encrypting web pages and REST API communications. Some CMS platforms provide free SSL to encrypt your pages. If not, then you need an API.
TLS/SSL only encrypts data when there is transfer of data. It doesn’t encrypt data that’s behind your API. But sensitive data should also be encrypted in the database layer as well.
You could also integrate a web application firewall (WAF) to monitor web traffic that identifies and prevents DDoS attacks or code injections as part of API security best practices.
5. Only Include Necessary Information In Responses
Sometimes there is a possibility that without intent an API response may expose information that hackers can use. To prevent this, ensure all responses sent to the end-user should only include information to communicate the success or failure of the request. The resource requested and any other information related to these resources.
Avoid sharing excess data. Because this can inadvertently expose private data, through returned resources or longwinded status messages.
6. Throttle API Requests & Establish Quotas
An API can impose rate-limiting to prevent brute-force attacks like DDoS. This can control the number of requests to the API server at any given time.
There are two foremost ways to rate-limit API requests: that is using quotas and by throttling. What quotas does is, it limits the number of requests that can be accepted from a user over a span of time. While throttling slows down a user’s connection. But it would still allow them to use the API.
Both these methods would permit normal API requests but it would prevent flooding of requests that would be intended to disrupt, or as unexpected request spikes in general.
7. Log API Activity
Up until this time you would have noticed that we’ve covered preventive and proactive methods for defying API threats as part of API security best practices. However, when a successful hack on your system occurs you would be keen to trace the source of the attack so that you may take necessary steps for the future and to report the problem as well.
This is the essential reason to log all API activity. If attackers do rupture your protections, you can always evaluate how they got it and what is it that they have done. Last but not the least an attack should be utilized to further strengthen your API. This would hypothetically prevent similar incidents in the future.
8. Conduct Security Tests
It is advisable that firms should not wait until an actual attack to check on the safety aspects laid out and how they hold up. Instead, make sure to have ample time for security testing. During this time you should intentionally hack your APIs to expose their liabilities and vulnerabilities.
And also remember that testing isn’t a one off process, but should be performed at a regular frequency and on a routine basis, especially whenever your API is updated.
After an Engineering degree and a Diploma in Management I devoted 16+ years working in the automotive industry. My innate skill and extreme passion in writing, encouraged me to adopt it up as a profession. I have been writing for more than 10+ years in the software industry. The 400+ blogs I published are informative, exhaustive and interesting to a professional and causal reader.









