Everyday APIs are working behind the scenes to provide a fulfilling digital experience to every user.
The flight travel you bought online, a recipe you shared on Facebook, and a cheap movie ticket you booked are all thanks to APIs.
API security helps flawlessly deliver integrated user experience from one device to another presenting a treasure of business opportunities.
An Application Programming Interface (API), is a software-to-software interface. Applications are provided with a secure and standardized path by APIs to work with each other and deliver information or functionality requested without manual intervention.
As expectations for effortless user experience increase, companies are looking at APIs to deliver further value to consumers in a jiffy. By leveraging APIs to access certain data, piece of code, software, or services, you can enhance the functionality of your product plus save time and money.
If the application providing the resource can provide what the client wants, then the API will return what is needed or a status code which means done. If the server isn’t able to complete the request, then the API will return an error message.
Implementing new APIs for an online application is a wonderful experience. Third party developers’ benefit while integrating with another app. Clients also benefit from an app’s integration, and it’s profitable as more users get drawn to the platform.
But hackers too are keeping watch for new APIs as it is an opportunity for them to exploit the info stored on servers.
What Is API Security?
API security is a manner of protecting APIs from abuse or cyber-attacks. API security ensures all requests that are processed by the API are legitimate, valid, and responses from the API are protected from interference or exploitation.
APIs aim to facilitate (often private) transfer of data, between a system and an external user. Therefore, a poorly maintained and insecure API can cause loss of sensitive data.
We have heard time and again about billions of records being exposed due to cyber-attacks and insecure APIs.
API hacks have affected businesses such as FB, Venmo, Twitter and USPS. To stay safe and protect sensitive data, integrate API security principles.
Why Is API Security Important
Cyber security covers all online technologies, but APIs are placed between third-party developers and a resource. API security breakdowns are detrimental to both the application and its users. This is because the hacked endpoint provides access to sensitive info.
A hack-attack can cause financial loss and harm your brand image. Customers lose their trust and firms their credibility while using an insecure API. Third-party integrated apps too can get affected via an extension.
REST API security vs SOAP API security
Web API security takes care of the transfer of data through APIs that are connected to the internet. OAuth (Open Authorization) is an open standard to delegate access. What it does is permits users to provide third-party access to web resources.
This is without having to share passwords. OAuth is the technology standard that allows sharing of lets you share any video to your social networks through a one touch share button.
Most API implementations are of 2 types: REST (Representational State Transfer) or SOAP (Simple Object Access Protocol).
REST API uses HTTP as well as support (TLS) Transport Layer Security encryption. TLS is a standard that keeps an internet connection private and checks data sent between two systems (server to server, or server to client) is encrypted and unmodified.
This means if a hacker is trying to gather your credit card information from a shopping website, he can neither read your data nor modify it. To check if a website is protected with TLS – the URL begins with “HTTPS” (Hyper Text Transfer Protocol Secure).
REST APIs also use JSON, this file format that makes it easy to transfer data over web browsers. By using a combination of HTTP and JSON, REST APIs don’t have to store or repackage data. Hence it makes them faster than SOAP APIs.
SOAP APIs use built-in protocols called as Web Services Security (WS Security). These protocols define a set of rules guided by privacy and authentication. They use XML encryption, XML signatures, and SAML tokens to verify verification and sanction.
In general, SOAP APIs are praised for having more comprehensive security measures, but they need higher handling. Therefore, SOAP APIs are endorsed for firms handling sensitive data.
Types of API Cyberattacks
Common attacks against APIs
Stolen Authentication
The simplest way to access an API is to swindle it using the identity of an authorized user. Once the authentication token gets into wrong hands, access to resources are compromised and information is retrieved by appearing legitimate but with wicked intent.
Cybercriminals also sometimes try and guess authentication passwords. Or they may even break a frail authentication process to gain access.
Man-in-the-Middle Attack
A man-in-the-middle (MITM) attack is referred to the occurrence wherein a hacker intercepts an API request or the response taking place in between an end-user and an API.
Sensitive contents may be stolen during this communication like login credentials, payment information or the contents of the request/response could be modified.
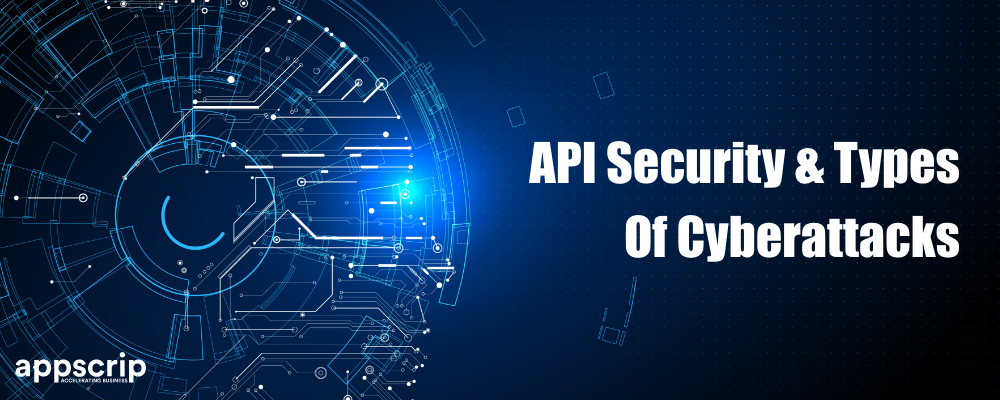
Code Injections
APIs with breaches in authentication and validation are vulnerable to code injections. Here usually an attacker sends a script to the application’s server using an API request. This script can expose or delete data, place false information, and harm an app’s internals.
Sometimes the term “SQL injection” maybe used. Code injection generally occurs on a SQL database.
Denial-of-Service Attack
A distributed denial-of-service attack is a cyber-attack that endeavours to slow or crash a website / web server / web service with API requests. This is done by overloading its server or network resources with web traffic.
A distributed denial-of-service (DDoS) attack is often times made concurrently from multiple malicious sources.
But these risks do not mean APIs will get redundant. Any online application seeking to integrate with a resource needs an API. And every new API is an opportunity for hackers to pilfer personal data. Therefore every software integration should undertake proper API-specific security measures.
After an Engineering degree and a Diploma in Management I devoted 16+ years working in the automotive industry. My innate skill and extreme passion in writing, encouraged me to adopt it up as a profession. I have been writing for more than 10+ years in the software industry. The 400+ blogs I published are informative, exhaustive and interesting to a professional and causal reader.