The onset of the pandemic has been a witness to huge growth in the eCommerce industry. More and more companies want to take their businesses online to overcome this debacle. This is basically because people are avoiding each other for fear of contagion. And security is the byword as it is a big concern.
Companies are worried and rightly so about choosing the right framework for their web development that would guarantee the security that is par excellence.
One of the advantages that Node.js presents is the ability to install additional modules. This ability is useful from the security point of view as it provides more opportunities to open back doors. But there is always a susceptibility that popular frameworks face, as there are more chances that hackers will scour around to find vulnerabilities.
Node. js is one such framework that can do wonders with both web and app development. It has become renowned due to its flexibility and being lightweight. It also guarantees unparalleled security features, if certain methods and practices are followed.
There are some security-related HTTP headers that should be set in every site. The headers are:
- Strict-Transport-Security – this basically enforces secure (HTTP over SSL/TLS) connections to the server
- X-Frame-Options provides clickjacking protection
- X-XSS-Protection enables the Cross-site scripting (XSS) filter that is built into web browsers
- X-Content-Type-Options prevents browsers from MIME-sniffing a response from the declared content-type
- Content-Security-Policy prevents attacks such as Cross-site scripting and other cross-site injections
Let’s take a look at some of Nodejs security best practices
Validating User Input For Limiting SQL Injections And QSS Attacks
The security challenge that is most basic for node.js is SQL injection. This is a process by which a hacker can execute SQL statements on any database. The best-advised practice to eliminate this threat is to never pass parameters from the frontend to the database query without proper monitoring. Always validate the values that the user provides.
Another form of common security concern is QSS attacks. This is also known as cross-site scripting. In this, a hacker gets an opportunity to execute any JavaScript code. Validation of the user input is the primary step that usually helps with a QSS attack.
Getting Rid Of Brute Force Attacks
A brute force attack means that the hacker generates millions of passwords at the same time in the hope of guessing the correct password. It is a cryptographic hack and is also called an exhaustive search.
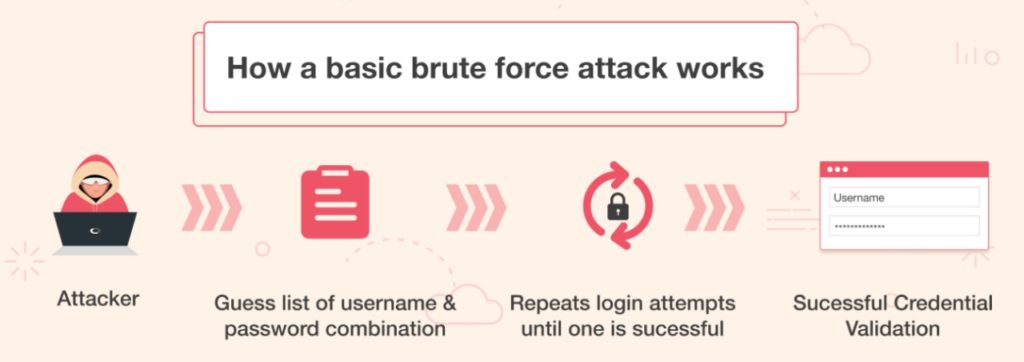
To get rid of such attacks in node.js, you can consider using the bcrypt.js package. It helps in guarding the passwords stored in the database. You can also consider limiting the number of requests coming from a single IP.
Get Security Against Denial Of Service Attacks
In a denial of service attack (DoS), hackers try to crash the system by generating a large amount of traffic. This can shut down the system, making it unavailable for the target audience.
This overloading of the system can be secured by implementing a limiting factors function. This function can limit the number of requests made by a user. This reduces the load on the system thereby preventing it from crashing.
Prevent Your Data Leaks
You cannot trust your front end in both circumstances such as sending data to it and receiving data back from it. Attackers can easily manipulate your system to get secure data sent from the backend.
The solution that is available to solve this problem is a time consuming one but it is pretty effective. Consider sending only the required amount of data. Do not retrieve more than necessary information from the database.
Utilize Security Linters
Are you aware that you can catch security susceptibilities even while writing code? This can be made possible by employing linter plugins like eslint-plugin-security. The linter plugin informs you of any unsafe code practices that you have included while coding.
Utilize Multi-Factor Authentication
A Microsoft study has found that your account is 99.9% safe if you use multi-factor authentication. MFA is an authentication process wherein an individual is given access to a system after presenting only two or more pieces of digital evidence.
In NodeJs security best practices as well, this feature is highly effective in limiting password hacks. Experts also recommend using stronger passwords for higher security.
Handling Errors In Node.js
There are many security errors in Node.js that can be solved easily. Some of them are:
- You shouldn’t run the full error object to the client. This is because it may contain information that you do not want to expose. For example, paths, another library in use, etc.
- Attackers can find malicious requests that can crash your system frequently. These are requests that attackers keep sending repeatedly that can crash your entire Node.js code. For preventing this, wrap routes with the catch clause.
Broken Access Control
Broken access control can lead to unauthorized access by attackers. To protect against such a vulnerability, you need to secure your API as well as give the necessary attention to account authorization.
Automated security test cases can also help with access control. Make sure to give equal attention to both authentication and authorization in your Node.js code.
Regular Scanning Of Applications For Eliminating Open Source Vulnerabilities
Since the internet is flocking with open-source packages for the JavaScript ecosystem, it has become quite difficult to keep track of the versions and licenses of these open source packages.
This gives hackers a window of opportunity to introduce malicious code into your application. To prevent this, use the following in your Node.js code:
- The package manager provided solutions
- WhiteSource Bolt
Adequate Logging And Monitoring
Inadequate logging and monitoring can result in providing attackers with easy access to your database. You can overcome such attacks by adopting the below-mentioned techniques:
- Configure your applications and services to a centralized logging system. It helps in providing an audit trail for ongoing attacks or previously attempted data breaches.
- There are many monitoring tools that your engineering team can utilize to trigger security alerts whenever a set of predefined conditions are met. Prometheus is one such monitoring tool.
Don’t run Node.js as root
Combine the ability to run any JavaScript code via an XSS attack with Node.js running as root and you’ll end up with unlimited hacking vulnerabilities.
Living in the Docker and microservices world we usually forget how Node.js is literally executed. We assume it is easy to make it secure by spinning up a Docker container and hoping it’s isolated from the host machine. But remember using Docker doesn’t really mean that running Node.js as root is not a concern anymore.
To Conclude – Node.js Security Best Practices
We have seen above the eleven best practices to deal with vulnerabilities in Node.js security. As technology keeps getting innovative, security concerns will keep escalating.
Securing web applications is imperative, but having tight schedules can sometimes inhibit us from properly executing all stages. Hence consider it important to take security seriously at every step in the software development lifecycle, right from conception to production.
This will help developers build a more secure system for users.









