Remember there is much sensitive information sitting on your business server right now.
It involves all the data you pass back and forth with customers & clients. Do you know how to keep it safe? Tokenization vs hashing has an important role. Let’s find out.
Tokenization
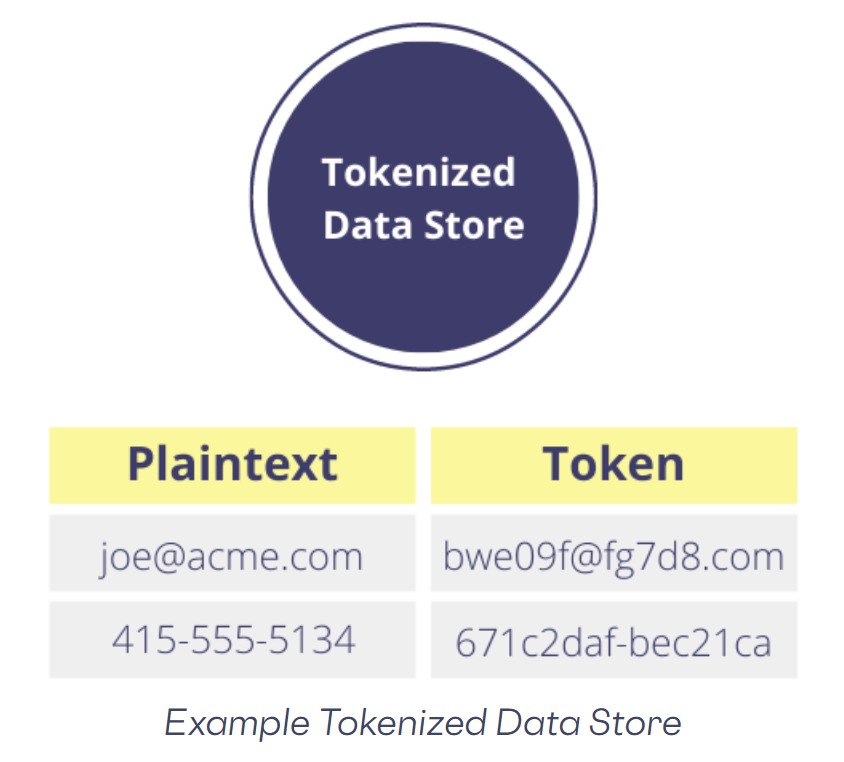
Tokenization is the replacement of sensitive data with quirky identification symbols but retaining all the essential information about the data without compromising its security. It helps minimize the data a business needs to hold.
Tokenization can be used with sensitive data of all kinds, including bank transactions – often used to protect credit card data, medical records to voter registration.
History
Since the beginning of early currency systems, coin tokens were used as a replacement for actual coins and banknotes. Examples being subway tokens and casino tokens, and substitutes for actual money. This is physical tokenization. The concept is similar to digital tokenization – acting as a surrogate for a prized asset.
As a recent development, tokenization was used in the payment card industry to protect sensitive cardholder data complying with industry standards. Since 2001, Trust Commerce has been credited with creating tokenization so as to protect payment card data.
Business Benefits of Tokenization
- Let’s begin with how to ensure hackers face difficulty gaining access to cardholder data. This is in comparison to older systems where credit card numbers were stored in databases which were exchanged freely over networks.
- This is compatible with legacy systems.
- It is not an immensely resource-intensive process.
- Data breach fallout risk is diminished.
- By propelling new technologies like mobile wallets, cryptocurrency, the payment industry becomes more convenient.
Hashing
Hashing in its true sense is used to safeguard business information & data. Hashing scrambles data and is intended to prove its authenticity. Deciphering key is non-existent. Once the data has been transformed, there’s no returning.
The controller can run a check on hashed data so as to determine if the subject matter hasn’t been accessed or altered while in storage.
Hashing & Its Working
The goal being protection but no decoding is involved. The process to determine alterations, doesn’t come with an automatic translation key.
In a business, customers often use the same passwords for multiple logins. This kind of data exposure could lead to numerous privacy concerns. A password hash system doesn’t anonymize data but protects the data while ensuring they’re used again.
Business Benefits of Hashing
- Assures that the data can’t be touched by hackers entering your server.
- One can use hashing to protect password data on the server.
- Then one can move to encryption to protect users’ downloads once they have gained access.
- Most adjustable method of retrieving data compared to any other data structure.
- Hashing is undoubtedly quicker than searching for lists and arrays and it doesn’t define speed.
Tokenization vs Hashing
Honestly, conceptually, they are very different serving different and unique purposes.
- Tokenization is a process where one tries not to possess the data. It’s a proxy to sensitive information with equivalent non-sensitive information which is the token. In the case of merchants using credit card numbers, instead of encrypting the information one stores it and assigns a key. Just think of it as a vault.
- Vaultless Tokens: Another kind being, instead of storing the sensitive data in a secure database, vaultless tokens can be stored using an algorithm.
- Hashing in business is when you take the information and run it through an algorithm. Whether it’s a single SSN or your name, one will end up with a unique code of numbers to represent the data. As with tokenization, the company is not required to behold the data.
Hashing has limitations for sure –
- There are certain data like SSN with finite values that shouldn’t be hashed, especially regularly accessed data.
- Another problem being, the one who uses hashing doesn’t always sweep out the system of non-hashed data.
The decision to use tokenization or hashing or any other process called encryption cannot be seen by executives as just a technical or cost issue as it’s very much a legal issue, therefore counsel should be approached, which may surpass the cost.
Certain Firms Prefer Hashing Rather Than Tokenization / Encryption
- Hashing is cheap, and encrypting data is challenging as it involves key management.
- Encryption is changing with time. Years ago what was applicable are now unsafe, so keeping a track of time while encrypting data becomes essential.
- Encrypting data securely through databases in constant use is a notable technological challenge.
- With tokens, one still has to protect the entire system under the credit card industry regulations which definitely does not make it a simple alternative to encryption.
Though, out of hashing/token & encryption methods, only encryption will help you avoid the state notification laws in case of a data security breach. In case of a future data breach, the data would become redundant in case of encryption, therefore still protected.
Legally one has a license, hence need not report the breach.
Conclusion: Tokenization vs Hashing
Now, mostly all companies are constructively trying to comply with state and federal regulations to rationally safeguard customer data in their purview and control. Encryption is a challenge in case of data security for most clients.
The truth or even the most practical point is customers often avoid best practices and pursue more cost-effective alternatives. Which is usually hashing over tokenization.
After an Engineering degree and a Diploma in Management I devoted 16+ years working in the automotive industry. My innate skill and extreme passion in writing, encouraged me to adopt it up as a profession. I have been writing for more than 10+ years in the software industry. The 400+ blogs I published are informative, exhaustive and interesting to a professional and causal reader.